Some info about the machine you will find below:
It would be great to find some webapp... Checking...
"Great" - "found 1" :|
"More."
Hm... I was wondering if there is anything else then 'submit.php':
Hm.. ;]
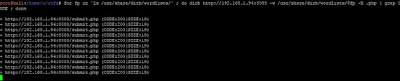
Well... you will find the way. I used the Burp (as usual):
After a while we should find new target:
(It reminds me that some time ago I had a pleasure to test a pretty similar platform used later for 'code review' too (let's say;])). That's why my first shot was to try some 'import pty;pty.spawn...' trick but unfortunately - no luck this time.
Then I decided to prepare some simple bindshell code (some snippets you can find here).
The code I used (will also be available at github):
Ok, let's start netcat in other terminal window (nc -lvvp 443) and copy the code to the 'Code review'.
We are here:
In my opinion if I will 'submit' the code now, we should achieve remote shell (in nc). Checking:
Let's get some more details about the situation here:
So far, so good.
(By the way, as you can see, kernel is 'old enough' to ("probably" ;) )be exploitable - for example...
At this stage you can of course go via the short way and r00t the machine immediately but I believed that this is not the case this time...) So...
First overview of mike's $HOME directory:
rws - cool. Checking (after you will check 'check_code.sh' script ;]
) with 'strings' first (maybe we will find the pass like the last time):
Ok, let's check one detail more about the program - the owner:
After a while of checking the program, we should find some errors. For example nice and warm format string bug:
If there is a way, exploiting the program should give us a shell with john's privileges. Let's see what we can do here:
Next (reading param value):
Overwriting GOT for printf():
Now we need to finish the payload to get the system()'s address instead of 0x00000004.
For the quick 'cheetsheat' of how to do it - you can send thanks (or beers;]) to leonizja.
Now we are here:
Next:
Bingo.
At this stage I decided to add my (new, regenerated for this) ssh-keys and add it (id_rsa.pub from my .ssh directory) to mike's authorized_keys to log in via normal SSH. Checking:
Cool. We're in. :]
Ok, for now (we have write access to mike's dir too, so ) we can see if our small poc will help us to overwrite printf's GOT:
Re-check:
Good. Now we need to put here a system address. Rewriting kode.py:
Now we are here:
Preparing new poc to accomplish the task:
...after the whole math I still wasn't able to run /bin/sh. I decided to run the poc with strace to (maybe) see something more:
After the symlinc wasn't able to do the job, I decided to create small wrapper in C:
(P.S. after a while I saw that we need also add another line to chmod to 4777 our /tmp/rap file. Rewrite your rapper.c a little bit and add new system().) We should be somewhere here now:
There is still something to re-check... (export PATH needs to be 'exported' to PATH:/home/mike. Then you should run the poc against my_first.)
Cool. Seems that our formatstring poc worked. Let's check created wrapper in /tmp:
So now we escalated our privs to the new user - john.
At this stage I decided to escalate to root and see the flag mentioned in the description of this CTF.
To do that I used one of the exploits for kernel mentioned before - CVE-2015-1328. Results you'll see below.
Because there was no wget or GET - I used the trick with netcat again:
Checking:
We got it!
To be honest great CTF. I was surprised to see format string to do so for me (I don't like formatstring so much ;]) it was a cool challenge. Big thanks goes this time to Knapsy - the author.
Another big thanks goes to VulnHub Team for hosting such cool game(s).
Cheers































Brak komentarzy:
Prześlij komentarz