Internet Explorer 8 is prone to remote denial-of-service. Below the poc and few details:
piątek, 27 maja 2016
MS Office 2010 - DoS in Publisher - #3
Publisher (from MS Office 2010) is (again) prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@26.05.2016
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@26.05.2016
czwartek, 26 maja 2016
Few pocs for IE8
I assume that this is probably useles now so for education purpose only, you will find few
proof-of-concepts (described by !analyze as "not", "probably" and "exploitable") below:
proof-of-concepts (described by !analyze as "not", "probably" and "exploitable") below:
MS Office 2010 - DoS in Publisher - #2
(AFAIK it's already published but without details.)
Below again a little bit more and poc:
Below again a little bit more and poc:
MS Office 2010 - DoS in Publisher
Publisher (from MS Office 2010) is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@07.05.2016
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@07.05.2016
środa, 25 maja 2016
Notes - ASM source
Looking for ASM hints? Try here:
* Intel® 64 and IA-32 Architectures Software Developer’s Manual Volume 2 (2A, 2B & 2C): Instruction Set Reference, A-Z
* Here about the registers
* and here about the opcodes
If you want to add something here, drop me an email or leave a comment.
Cheers.
* Intel® 64 and IA-32 Architectures Software Developer’s Manual Volume 2 (2A, 2B & 2C): Instruction Set Reference, A-Z
* Here about the registers
* and here about the opcodes
If you want to add something here, drop me an email or leave a comment.
Cheers.
Crackme by ZaKne
In C/C++ section here, you will find another crackme - this time it's called "ZaKne's crackme".
It's pretty simple to do:
It's pretty simple to do:
wtorek, 24 maja 2016
poniedziałek, 23 maja 2016
Smash The Tux 1.0.1 CTF Writeup - 0x00
First stage of SmashTheTux CTF. Thanks 1ce7ea and Vulnhub!
Let's install VM and start the first challenge:
Let's install VM and start the first challenge:
niedziela, 22 maja 2016
Seattle v0.3 CTF writeup
You should check the Seattle v0.3 CTF - it is another great VM this time from GracefulSecurity.
(I found it few weeks ago on vulnhub.com and now it was a time to do it.) It was again great
pleasure and a lot of fun. Thanks!
So, after quick nmap...
(I found it few weeks ago on vulnhub.com and now it was a time to do it.) It was again great
pleasure and a lot of fun. Thanks!
So, after quick nmap...
sobota, 21 maja 2016
Pentester Lab CTF - Axis2 and Tomcat Manager
Here we have another one (I believe already solved) CTF from VulnHub. I had a pleasure to check it during one internal CTF prepared for the meeting with the new customer. Below you'll find a quick writeup:
Prepare the VM and run nmap against it:
Prepare the VM and run nmap against it:
Pentester Lab CTF - Web For Pentester
Another cool VM from Pentester Lab called "Web For Pentester". Just like before, you can find the ISO on vulnhub.com. Let's find out what we can do with this one. Prepare VM and let's get to work.
As always, let's scan it first to see if there is an interesting service(s) running:
As always, let's scan it first to see if there is an interesting service(s) running:
Pentester Lab CTF - From SQLi to PostgreSQL shell
If you're looking for cool CTF's that you can play offline (or during the travel) this site is definitely for you. :) Today we will try if there is a way to get shell on the VM box prepared by Pentester Lab.
Thanks for preparing this!
Run and go
VM is ready, running, so let's scan it:
Thanks for preparing this!
Run and go
VM is ready, running, so let's scan it:
Crackme by BioHazard
Hey. Another nice crackme was released by BioHazard. You can as always find it here.
To be honest this was a little surprise. I was wondering by there is still an error, and that's how I found...
To be honest this was a little surprise. I was wondering by there is still an error, and that's how I found...
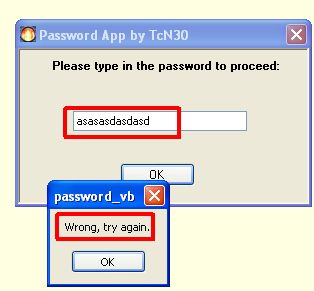
Crackme by TcN30
Ok, here we'll solve another simple crackme from this site. This one is prepared by TcN30 (thanks!) and is called "password_vb.exe". Let's do it:
Crackme by The Rapture - FishME
During my last visit on www.crackmes.de I found 'few' .NET crackmes to do. I decide to check them (starting from few basics) and describe them here as a small analyze (as well as a memo for me). That's how I found crackme by Rapture (thanks!)
Idea was to get the serial. Unfortunately the serial was hardcoded inside the app so quick journey with .NET Reflector, and you will find it:
Cool. Next time we will try something else...
Idea was to get the serial. Unfortunately the serial was hardcoded inside the app so quick journey with .NET Reflector, and you will find it:
Cool. Next time we will try something else...
piątek, 20 maja 2016
Subskrybuj:
Komentarze (Atom)