We will (again) start here:
I used 'latest' available version - 5.6.9 - for VirtualBox, downloaded here.
As you (probably;)) read/remember, in scheduled reporting we have a persistent XSS. Sometimes when I found a bug 'related to OWASP' (so for example: XSS) I'm trying to check the source code of webapp ('if available') to look for similar cases:
So, to see a bigger picture:
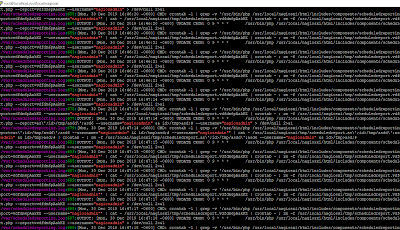
As you can see on the screen:
- we can create file on server
- we can inject some garbage on the filename (like '> or ">)
- we are using php 'to run command'
Cool. My goal was to get RCE here. ;)
So the case was:
- attacker (logged-in normal/registered user) will inject malicious payload in scheduler
- scheduler will run attached code when using cron*
*(in source you will see that our injection is possible when script will do: rm -f <ourString> but we will get to that later;))
Checking again (and again...):
Still nothing. The case is: how to inject a string to cron-not-to-php? Hm... I (still) don't know yet.
I tried to use the same command (in other shell windows) as was the command injected to the (created) script. I was wondering, maybe I'll find the injection string this way...
Still - nope.
So after a 'day with Nagios VM' we should be somewhere here, reading logs ;)
we are here again:
After few more times/requests I decided to check logs again... this time I found this:
Well. Yes, /etc/issue is printed to the log file ;D
As you can see, payload should write file to /tmp/qwe. And in fact, it is true, but we are looking in wrong /tmp/ directory. ;) Check it out:
So no we should be somewhere here, verifying:
I used revshell from pentestmonkey (thanks!):
Quick configuration and we should be here:
That's all. ;)
If you like the post (and my blog) - remember that now you can send some donate$ ;)
Happy new year and see you next time!
Cheers











It's either a corporate-state political problem or a labor-union solidarity problem.
OdpowiedzUsuń>>> Nagios provides enterprise-class Open Source IT monitoring, network monitoring, server and applications monitoring. Download Nagios ...
I see the term "enterprise class" and with all that "management-level" monitoring there is somewhat of a heavy slur cast on the whole idea of "open source."
They've definitely got inside help at the big tech firms for the zero-day issues, including a wink and a nod from management for poor coding practices.
The guys getting paid to crank out code often don't even appreciate the idea of open source, and any association between open source and security vulnerabilities is a plus to their proprietary-code-based job security.
It's a security firm. They don't want to work themselves out of a job. You got too much of an oil change at that service station.
Interesting 'point of view'. ;)
UsuńThanks for watching.