Let's start here:
Ok, it looks pretty similar. Let's download that binary and run file and strings against it:
Next:
I was wondering if this is it in this sample; we can see a request and (the same) server IP address. Let's check the IP address:
As we can see this is not a new (attacking) server:
(Yep, I know PEiD will not help you a lot with *nix files... but I just like to drop a binary there ;))
Let's present our girlfriend to the binary:
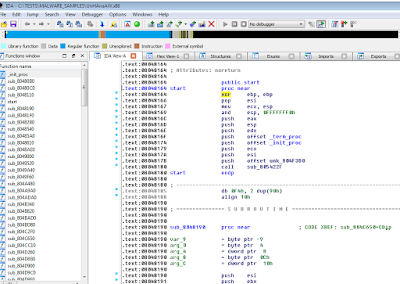
After a while we should be somewhere here:
Click F12 (to see the strings) and you should quickly find a function to (do a POST) request:
I changed the name to send_POST() like you can see below:
Request to mentioned URL can be found on Google:
Let's see the details:
Next:
Looks pretty similar to our case:
More details you can find here:
Or at SecurityFocus:
Special thanks to my Patreon:
- Daniel
You are AWESOME! ;)
See you next time!
Cheers,
Cody
















Brak komentarzy:
Prześlij komentarz