Hi
środa, 28 grudnia 2016
poniedziałek, 26 grudnia 2016
Automated scans with OpenVAS and Kali
I was
wondering if we can run (some kind of ) an “automated scan”, out-of-the-box in
Kali Linux. Version I used was updated to the latest one (for 26.12.2016, so 2.0). Here we go...
niedziela, 27 listopada 2016
Crontab with iptables
I created a small code in bash to check for any new requests in Apache's logs. Found IP(s) will be blocked by iptables.
sobota, 26 listopada 2016
Basics of ARM/MIPS malware analysis
On one of my honeypot's I found an interesting log line, related to some URL-encoding. I was wondering what's there if I will be able to decode that GET...
Windows logs in PowerShell
I was wondering if anyone of you remember the zap2.c :) I couldn't find "zap2.c for Windows" so I was wondering if I can do something like that... in PowerShell... in Windows... ;) This is what I found:
wtorek, 8 listopada 2016
Playing Winamp
After a while when I started to fuzz Winamp
(again), I found my old directory with some (about ~300 files) results, all
ready to ‘check them later’… so I think ‘now’ is a good time to do it. Let’s
get to work.
środa, 2 listopada 2016
sobota, 29 października 2016
HTTP Server fuzzing with Burp
In the middle of time I was working on some HTTP server fuzzer created in python. I was wondering if I can get similar results when I will use only Burp proxy. Below example results.
poniedziałek, 24 października 2016
headHunter.py
After reviewing "Python Web Penetration Testing Cookbook" I modified one skeleton script found inside the book. Below you will find some results:
niedziela, 23 października 2016
Playing Assasin's APK
In the middle of time I was checking some sample
malwares from excellent Contagio’s Blog. This time I decided to get
back to APK files. Below you will find small analysis of Assassins_Creed.apk.
Playing with Contagio
(Still) during my „little
break”, I found some directory on my disk with few
samples from excellent Contagio’s Blog. I decide to check few of
them, this time related to web attacks.
Crash gdb in Kali
Couple of
few days ago I tried to finish one cool CTF (writeup will be here as soon as I
will finally finish it;)). Because I had some troubles with that, I decide to
take a ‘little break’ and move to “something else”, which was… debug in Linux.
;)
piątek, 16 września 2016
SQL injection in latest e107 CMS
Bug exists in admin's panel. It's possible to exploit only when you have admin's credentials. Full details described below...
Tr0ll 1 - CTF
wtorek, 13 września 2016
niedziela, 11 września 2016
6Days Lab CTF
Friend of mine asked me if I know this CTF. I decided to check it during the weekened. Below quick review...
sobota, 10 września 2016
Local resource enumeration via XSS
Probably you all already know how to "Hack Intranet Websites from the Outside" (if not, google for Jeremiah Grossman and RSnake - you can start here - and read about some attacks from 2006 and 2007). ;) There you will find similar usage of JavaScript as you can find below:
DVL Warmup poc
Yesterday I was playing with an old ISO called Dam Vulnerable Linux. If you're learning some binary exploitation, a nice 'warmup exercise' can be found here:
piątek, 9 września 2016
Lord Of The Root - CTF
First of
all: big thanks for the author for preparing this CTF. Man, I had no
idea that Frodo is a hipster! ;D
poniedziałek, 5 września 2016
Bitbot CTF
In the middle of the other activities
and projects, I decide to sit down for a while and check another CTF. This time
I decided to try Bitbot. Found again on VulnHub – thank you guys. Also big
thanks for the author (bwall) for preparing this game! So… Let’s get to work.
poniedziałek, 22 sierpnia 2016
Testing SQL injections in com_virtuemart 3.0.14
Yesterday after I finally finished Jomlash module I decide to check the latest com_virtuemart component. The version I tried was 3.0.14. As far as I know, “the latest” one …
sobota, 20 sierpnia 2016
joomlash - new test in grabash.py
During couple of last few days I had a chance to check grabash
code again. I am aware that this is still not even 'first' final
version ;) so there is always something 'todo' or to fix to get better
results from the scan. So, yeah, any feedback is welcome.
czwartek, 18 sierpnia 2016
wtorek, 16 sierpnia 2016
Axis2 LFI module for CTF
Few weeks ago I tried to solve Axis2 CTF from VulnHub. It was a lot of fun. As far as there is a grabash, I decided to create small module for Metasploit to exploit LFI bug in that virtual machine...
niedziela, 7 sierpnia 2016
Small script for Metasploit in Kali
During last pentest I was wondering how can I automate few tasks. Idea is based on...
piątek, 29 lipca 2016
Exploiting Kali2 - Part 1
Hi,
few days ago I was waiting for another results from one of the fuzzers. I decided to start
another VM - this time with Kali2 - and try to find few bugs to play...
few days ago I was waiting for another results from one of the fuzzers. I decided to start
another VM - this time with Kali2 - and try to find few bugs to play...
piątek, 22 lipca 2016
bikoz.py
Couple of days ago I decided to
write some “small script in Bash” to automate a little bit the work related to
(so called) “information gathering” during the pentests. I decided to choose
Bash because I’m working with it, most of time
during the day anyway, so…
wtorek, 19 lipca 2016
niedziela, 17 lipca 2016
sobota, 16 lipca 2016
piątek, 15 lipca 2016
czwartek, 14 lipca 2016
Irfan View - Crash - WMA heap crash
WMA crash found 09.04.2016 during IrfaView fuzzing... Details below:
Irfan View - Crash - TIFF case
TIFF crash found 09.04.2016 during IrfaView fuzzing... Details below:
Irfan View - Crash @MSCTF!TF_CheckThreadInputIdle
I found a crash in IrfanView. The most interesting for me this time was unpacking original i_view32.exe to new exec (1,5MB). Details of the crash you will find below.
czwartek, 7 lipca 2016
niedziela, 5 czerwca 2016
NULL Pointer Dereference in MS Publisher 2010
MS Publisher 2010 - NULL_CLASS_PTR_DEREFERENCE
-----------------------------------------------------------------------
Found : 04.06.2016
-----------------------------------------------------------------------
Open your Windbg and run MSPUB.exe. Attach debuger to Publisher.
Ctrl+S to check the symbols, and here we go:
dbg> srv*c:\symbols*http://msdn.microsoft.com/download/symbols
-----------------------------------------------------------------------
Found : 04.06.2016
-----------------------------------------------------------------------
Open your Windbg and run MSPUB.exe. Attach debuger to Publisher.
Ctrl+S to check the symbols, and here we go:
dbg> srv*c:\symbols*http://msdn.microsoft.com/download/symbols
piątek, 27 maja 2016
IE8 Divided by zero
Internet Explorer 8 is prone to remote denial-of-service. Below the poc and few details:
MS Office 2010 - DoS in Publisher - #3
Publisher (from MS Office 2010) is (again) prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@26.05.2016
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@26.05.2016
czwartek, 26 maja 2016
Few pocs for IE8
I assume that this is probably useles now so for education purpose only, you will find few
proof-of-concepts (described by !analyze as "not", "probably" and "exploitable") below:
proof-of-concepts (described by !analyze as "not", "probably" and "exploitable") below:
MS Office 2010 - DoS in Publisher - #2
(AFAIK it's already published but without details.)
Below again a little bit more and poc:
Below again a little bit more and poc:
MS Office 2010 - DoS in Publisher
Publisher (from MS Office 2010) is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@07.05.2016
Attackers can exploit this issue to crash the affected application.
-------------------------------------------------------------------------------------------
Found by : code16@07.05.2016
środa, 25 maja 2016
Notes - ASM source
Looking for ASM hints? Try here:
* Intel® 64 and IA-32 Architectures Software Developer’s Manual Volume 2 (2A, 2B & 2C): Instruction Set Reference, A-Z
* Here about the registers
* and here about the opcodes
If you want to add something here, drop me an email or leave a comment.
Cheers.
* Intel® 64 and IA-32 Architectures Software Developer’s Manual Volume 2 (2A, 2B & 2C): Instruction Set Reference, A-Z
* Here about the registers
* and here about the opcodes
If you want to add something here, drop me an email or leave a comment.
Cheers.
Crackme by ZaKne
In C/C++ section here, you will find another crackme - this time it's called "ZaKne's crackme".
It's pretty simple to do:
It's pretty simple to do:
wtorek, 24 maja 2016
poniedziałek, 23 maja 2016
Smash The Tux 1.0.1 CTF Writeup - 0x00
First stage of SmashTheTux CTF. Thanks 1ce7ea and Vulnhub!
Let's install VM and start the first challenge:
Let's install VM and start the first challenge:
niedziela, 22 maja 2016
Seattle v0.3 CTF writeup
You should check the Seattle v0.3 CTF - it is another great VM this time from GracefulSecurity.
(I found it few weeks ago on vulnhub.com and now it was a time to do it.) It was again great
pleasure and a lot of fun. Thanks!
So, after quick nmap...
(I found it few weeks ago on vulnhub.com and now it was a time to do it.) It was again great
pleasure and a lot of fun. Thanks!
So, after quick nmap...
sobota, 21 maja 2016
Pentester Lab CTF - Axis2 and Tomcat Manager
Here we have another one (I believe already solved) CTF from VulnHub. I had a pleasure to check it during one internal CTF prepared for the meeting with the new customer. Below you'll find a quick writeup:
Prepare the VM and run nmap against it:
Prepare the VM and run nmap against it:
Pentester Lab CTF - Web For Pentester
Another cool VM from Pentester Lab called "Web For Pentester". Just like before, you can find the ISO on vulnhub.com. Let's find out what we can do with this one. Prepare VM and let's get to work.
As always, let's scan it first to see if there is an interesting service(s) running:
As always, let's scan it first to see if there is an interesting service(s) running:
Pentester Lab CTF - From SQLi to PostgreSQL shell
If you're looking for cool CTF's that you can play offline (or during the travel) this site is definitely for you. :) Today we will try if there is a way to get shell on the VM box prepared by Pentester Lab.
Thanks for preparing this!
Run and go
VM is ready, running, so let's scan it:
Thanks for preparing this!
Run and go
VM is ready, running, so let's scan it:
Crackme by BioHazard
Hey. Another nice crackme was released by BioHazard. You can as always find it here.
To be honest this was a little surprise. I was wondering by there is still an error, and that's how I found...
To be honest this was a little surprise. I was wondering by there is still an error, and that's how I found...
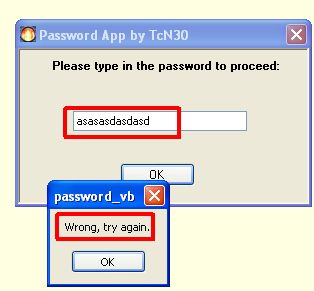
Crackme by TcN30
Ok, here we'll solve another simple crackme from this site. This one is prepared by TcN30 (thanks!) and is called "password_vb.exe". Let's do it:
Crackme by The Rapture - FishME
During my last visit on www.crackmes.de I found 'few' .NET crackmes to do. I decide to check them (starting from few basics) and describe them here as a small analyze (as well as a memo for me). That's how I found crackme by Rapture (thanks!)
Idea was to get the serial. Unfortunately the serial was hardcoded inside the app so quick journey with .NET Reflector, and you will find it:
Cool. Next time we will try something else...
Idea was to get the serial. Unfortunately the serial was hardcoded inside the app so quick journey with .NET Reflector, and you will find it:
Cool. Next time we will try something else...
piątek, 20 maja 2016
Subskrybuj:
Komentarze (Atom)