After the last VM I decided to check another one - this time prepared by Viper, called Sedna. More details you will find here shared thanks to the VulnHub. Here we go...
When VM is ready, we should be somewhere here, during the scan:
After a while, we can check dirs/files presented in output by GoBuster:
And what do we have here:
Checking:
Hm... "never heard about it" - well... ;]
Checking:
Ok. Next:
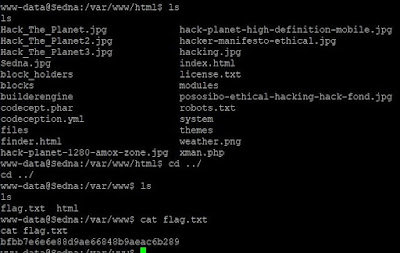
So I was wondering how to root that box. Next idea was to look what's inside the box (fo read by user I already have). That's how I found flag.txt ;]
Next thing was: if there is Tomcat (/manager) available for login I can: bruteforce the pass (nah...), use some misconfiguration bug to gain password(s)... Unfortunately I wasn't able to read it as www-data ;]
Next, should be easy:
... but it wasn't. ;] So after (few minutes and) the hint from the author:
I decided that it will not be the case this time and I need to look for something else. I decided to enumerate the OS and files inside webroot dir(s), maybe some new user(names) or hardcoded passwords... but no. ;]
Then I found that there is also a nice dirname inside /etc/ directory - chkrootkit:
I wasn't sure if there is anything published for this version, but after few seconds with Google you will find CVE-2014-0476 ;] and proof-of-concept available on Exploit-DB.
Checking:
...aaaand...
Badumtssss.... ;]
Now it was a lot easier to read the flag.txt in /root directory. ;]
Big thanks goes to the author (Viper) for preparing this CTF and to the VulnHub Team for sharing all of those games.
See you next time.
Cheers












Brak komentarzy:
Prześlij komentarz