Today we will start here:
Just like before - starting from admin user - I tried to look for some new bugs (like RCE). After a while I found in the logs this line:
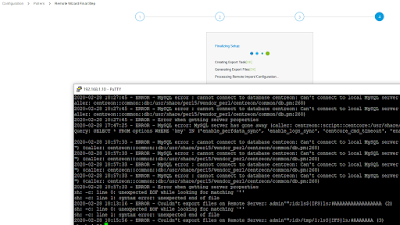
Because last time I used 'local poller', today we will use the Wizard to prepare a remote server. Here we go:
Should be enough to grep the logs ;)
Ok, so this was when I was looking for a reverse shell ;]
Like last time I found nice payload here. Next thing was to use ${IFS} again so I replace ' ' in notepad:
Now, with multiple putty windows prepared we can try to inject our super payload ;)
...aaaaand... nothing happened. ;D
It should be frustrating but not today ;) Here we go again:
Ok, we know there is no wget (so GET used instead), and it looks (above) like it should work like a charm... ;S
Checking again:
Ok, next:
As you can see we don't have a lot of space to use here. To save few 'letters' I move file again and again using different 'whitespaces' (like mentioned ${IFS}, + and so on...):
So after a while we should be somewhere here:
Mhm... great Neo. Try harder ;)
Yes... So:
Ok, so 'shell command should work' - right?
*No.
At this stage I still wasn't able to see the 'feedback information from the application' ;) Do you? ;>
*Yep, it was a 'valid payload' for (the lenght of) that field. :)
Next step? Obvious. Go to the next field - "Server IP address":
:)
Maybe you will find it useful (and/or maybe you will find more vulnerable fields there).
;)
See you next time!
Cheers




















Brak komentarzy:
Prześlij komentarz