We'll start here:
As you can see this malicious-word-file is still online so - be careful.
(Later I saw on VirusTotal that it was already uploaded in January - but we'll get back to that later.)
Anyway... ;] I decided to download it to Kali VM. This time I used fresh installed VM (I used VMware this time). As you can see - to proceed - I installed few tools and libs, for example:
After a while we should be somewhere here, testing olevba tool(s):
Output looks promising:
I tried to restart tools available in the package with different parameters (like mentioned below --deobf or --decode; see man ;)):
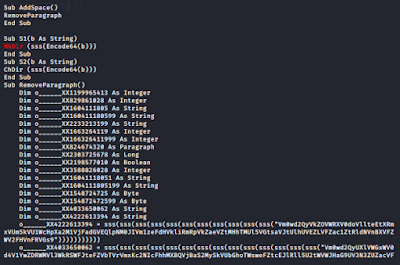
When I saw base64-strings I decided to check it out:
In the meantime I tried to collect as-much-details-as-I-can about the target-file (so I played a little bit longer with the tools inside DidierStevensSuite):
Here we go again... with new params ;]
After a while I decided to give it a try and register on Any.Run:
Malicious Word file uploaded:
Very first results - below:
Few seconds later we can see the whole path that malware took to proceed:
I must say it was pretty cool to watch all of the execution flows ;] Next one:
Next one (now we finaly see some connections ;]):
Cool enough to ask C&C about the weather and things like that... ;]
In the meantime I found that malware is trying to escalate privileges (more details I found on github):
Next window now looks like this:
(...10minutes later...)
Few more stats found online:
Network looks like a pretty active one ;] More from ASN:
In the meantime I found pretty nice picture generated by Any.Run
One of the tool I found online was of course OfficeMalScanner - if you don't know the tool (or the page) you should check it ASAP. (I switched from Kali VM to Windows 7 VM to use to tool.) Now we should be here:
Few more details I found when I was using SSView:
Next:
Few more checks:
...and I decided to send the file to Ida:
I started reversing the binary. Reading strings and imports and all of that and that's how I found this one string:
Looks like some IOC ;]
When I found AVE_MARIA string it was pretty obvious that the malware is alredy known:
Maybe you will find it useful.
Special thanks goes to my Patreon: Daniel.
Thanks! You are AWESOME! ;)
See you next time!
































Brak komentarzy:
Prześlij komentarz